
Graph Databases for Crime-Fighting: How Memgraph Maps and Analyzes Criminal Networks
Graph databases, such as Memgraph, are highly effective in crime-fighting and intelligence work because they excel at uncovering and analyzing relationships between entities, such as individuals, communication channels, and locations. In counter-terrorism and counter-intelligence operations, graph databases are often used to map out and analyze complex networks of individuals and their associations.
In this blog post, we’ll explore several real-world use cases where graph databases are used to fight crime and how Memgraph’s capabilities make it an ideal tool for mapping and analyzing these complex networks.
Memgraph helps connect the dots. It allows you to track individuals, communications, and locations in ways that other systems struggle to manage. And if police departments and intelligence services turn to graph-based solutions, Memgraph stands out for its ability to process complex relationships in real time.
The Challenge of Fighting Modern Crime
Criminals don’t operate in isolated silos. They communicate across borders, use multiple aliases, and leverage technology to hide their tracks. The problem? All that data is scattered across different platforms—phone records, social media accounts, GPS locations, emails. Tracking it all manually old school like you saw in Wire, is nearly impossible.
Even when agencies gather that data, traditional databases fall short. It’s one thing to know that two individuals have been in contact; it’s another to quickly map out how they’re connected to a broader network of suspects, locations, and transactions. Graph databases are great for such tasks.
How Graph Databases Solve Crime Problems
Graph databases are designed to handle exactly this type of challenge. Instead of forcing your data into rows and columns, a graph database is built to understand relationships. It’s a natural fit for law enforcement trying to untangle the complex web of a criminal organization.
With Memgraph, you can map relationships between people, locations, and communications in real-time. This kind of power means investigators can quickly understand who’s connected to whom, track the flow of information, and reveal hidden networks in ways that traditional databases can’t match.
Memgraph Use Cases in Crime Fighting
Mapping Criminal Networks
Imagine you’re an investigator trying to bring down a major drug trafficking ring. You’ve got some basic data: names, phone records, and addresses. But how do you piece it all together?
Memgraph lets you map these relationships in real-time. As new data comes in—such as a new phone number or a location ping—you can instantly update the graph to see how this new information fits into the existing network. The result? A comprehensive view of the organization that allows investigators to pinpoint the key players and take action faster.
Tracking Online Radicalization
Tracking online radicalization is like trying to find a needle in a haystack. The internet provides a massive platform for individuals to connect, but it also allows extremist ideologies to spread rapidly, often hidden in plain sight among millions of other conversations. Governments and law enforcement agencies are increasingly turning to graph databases to monitor this activity.
With Memgraph, you can map out how radical ideas travel through social media. Let’s say you’re monitoring a suspicious account that’s been sharing extremist content. That’s your starting point. Memgraph lets you follow that account’s interactions—who follows them, who shares their posts, who comments. Before long, you’re not just looking at one account but a network of accounts, all engaging with similar content, forming an echo chamber of radicalization.
The real power of graph databases like Memgraph comes into play when you start connecting these online interactions to real-world data, like phone numbers, email addresses, or even locations. By linking this information in real-time, agencies can track not only the spread of harmful ideologies but also identify recruiters and at-risk individuals before they take dangerous action.
Fraud and Financial Crime Detection
Follow the money. It’s a phrase that’s as relevant today as ever, particularly in cases of fraud and money laundering. But following the money isn’t always straightforward—criminals go to great lengths to cover their tracks.
Memgraph allows investigators to visualize financial flows between accounts, identifying suspicious patterns that may indicate illegal activity. Whether it’s a complex Ponzi scheme or a case of identity fraud, Memgraph can help untangle the web of transactions and connect the dots between the actors involved.
Phone and GPS Tracking
When investigators get access to phone records, they need to act fast. Whether it’s tracking a suspect’s movements or identifying their connections, time is critical.
With Memgraph, phone records and GPS data can be processed in real-time, allowing investigators to instantly see where suspects have been, who they’ve contacted, and when they’ve interacted with key locations. The result? A dynamic, up-to-date map of a suspect’s movements and connections.
Human Trafficking and Smuggling Networks
Human trafficking and smuggling operations are notoriously difficult to track. Victims, perpetrators, and accomplices often move between cities or even countries, leaving behind a trail of disconnected data.
Memgraph brings that data together. By linking transportation routes, communication channels, and financial transactions, investigators can map the entire network and identify critical nodes. This makes it easier to rescue victims and dismantle the operations behind these crimes.
Fraud Rings and Identity Theft
Fraud rings and identity theft operations are more sophisticated than they were 10-15 years ago. Criminals create networks of fake identities, use fraudulent documents, and route transactions through a web of accounts to cover their tracks. Traditional databases often struggle to detect the connections between these seemingly separate entities, but this is exactly where graph databases shine.
With Memgraph, you can track how those identities are linked to others—same addresses, shared phone numbers, overlapping bank accounts. Suddenly, what seemed like isolated incidents of fraud start forming a web, revealing the entire fraud ring’s operation.
It’s not just about detecting existing fraud either. Memgraph can help prevent future identity theft by flagging suspicious patterns. For instance, if several accounts are created using variations of the same name or address, the graph can quickly alert investigators to the potential of a larger fraud operation before it even takes off.
Read more about Memgraph use cases:
Why Memgraph?
So why use Memgraph for crime-solving specifically? Let’s break it down:
-
Real-time data processing - In crime-fighting, waiting minutes (or hours) for database queries can mean the difference between stopping a crime and chasing it. Memgraph processes data in real time, so you can act on new information instantly.
-
High-performance parallel querying - Investigators deal with huge datasets—phone records, emails, social media posts. Memgraph’s architecture allows for high-throughput parallel querying, so it scales with the complexity of the investigation.
-
Cypher query language - Memgraph uses Cypher, a straightforward query language. This means that even law enforcement analysts without deep technical backgrounds can quickly learn how to run queries and analyze the data.
-
Scalability - From small investigations to massive, multi-national cases, Memgraph scales as needed. Whether you’re analyzing a few individuals or a sprawling criminal organization, Memgraph can handle the load.
Algorithms To Help Fight Crime
The following algorithms listed below are either available directly in Memgraph or can be implemented using Memgraph's MAGE (Memgraph Advanced Graph Extensions) library.
-
Path Traversal Algorithms → used to analyze all potential routes in a network.
-
Breadth-First Search (BFS) - This algorithm helps find the shortest path between two nodes in a graph. In crime investigations, BFS can be used to trace communication paths between suspects, identify the shortest money transfer route in money laundering cases, or track a suspect’s movement across multiple locations.
-
Depth-First Search (DFS) - Unlike BFS, DFS explores all potential paths in a network. This can be useful for mapping out all possible routes a suspect could have taken or identifying multiple communication channels in a network.
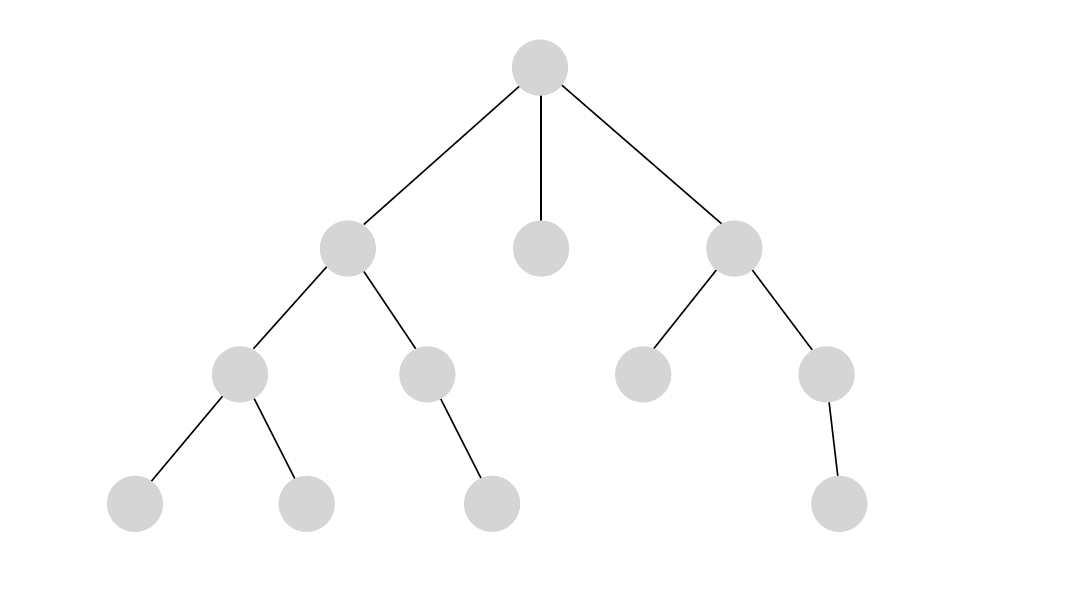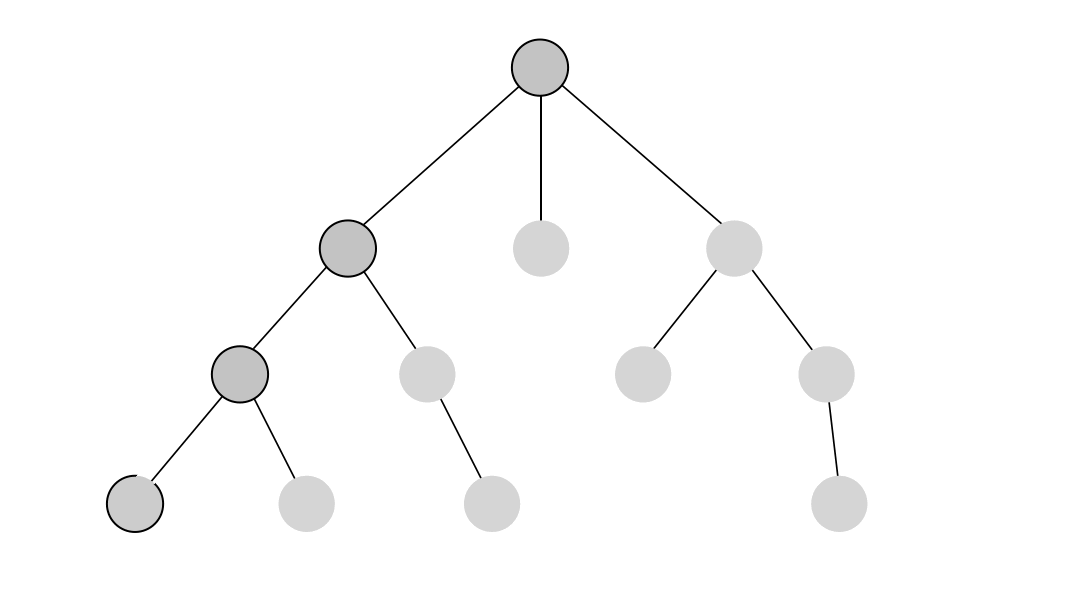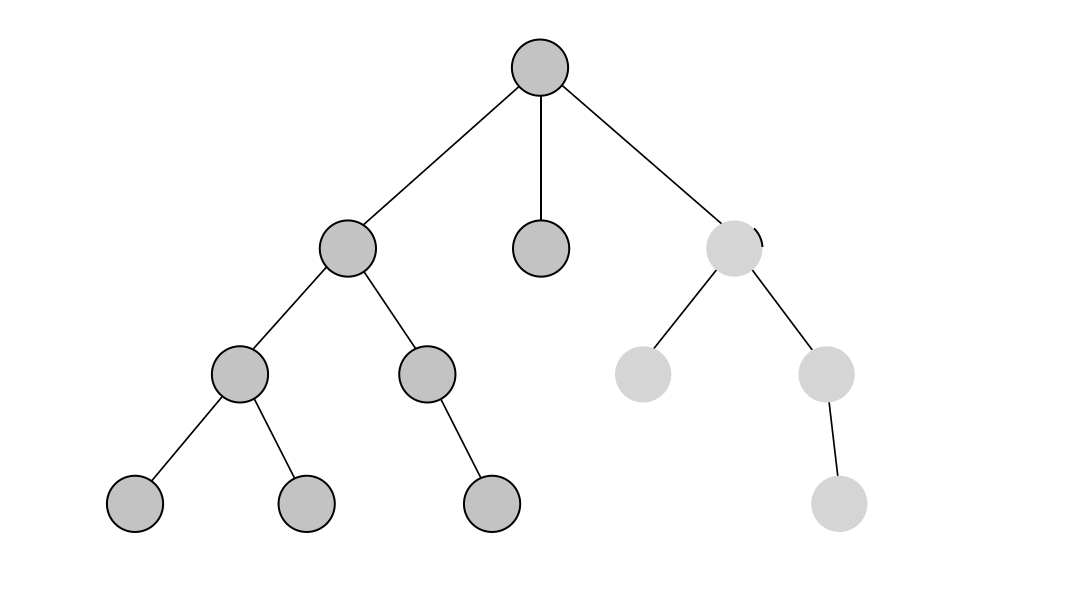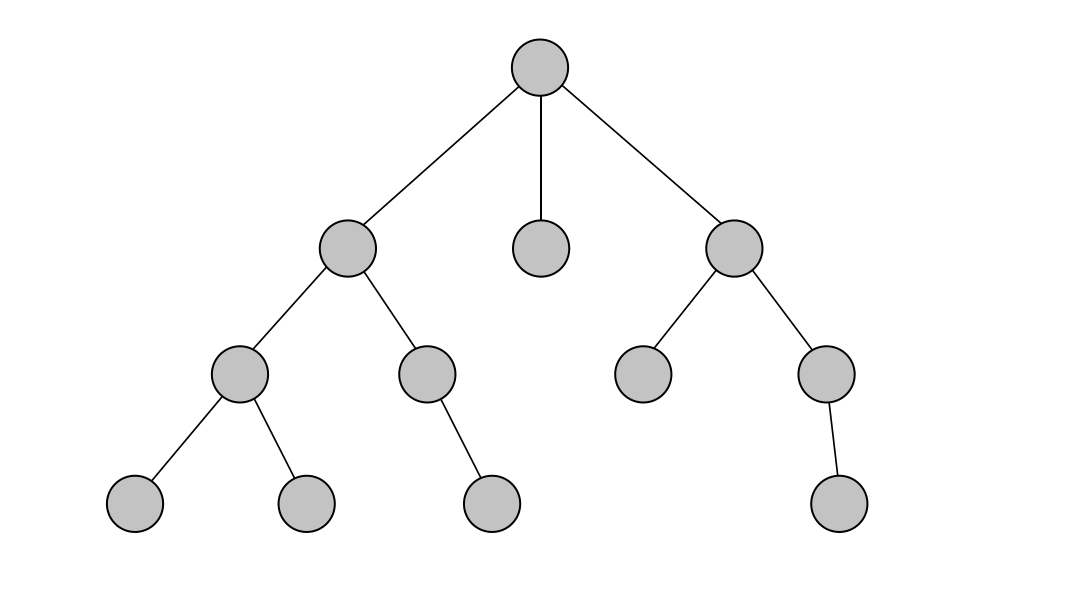
-
Weighted Shortest Path - This algorithm finds the shortest path while considering weights, such as time or cost. In crime investigations, it can be used to trace optimized routes, such as tracking financial transactions in a money laundering scheme while considering the amounts transferred. This algorithm is available through the MAGE library.
-
-
Centrality Algorithms → identifying key players in a criminal network.
Centrality algorithms, such as Betweenness Centrality and PageRank, help detect the most influential or central nodes in a network. This is essential for identifying leaders of criminal organizations, key connectors in fraud rings, or influential radicalizers in online extremist groups. Available through the MAGE library.
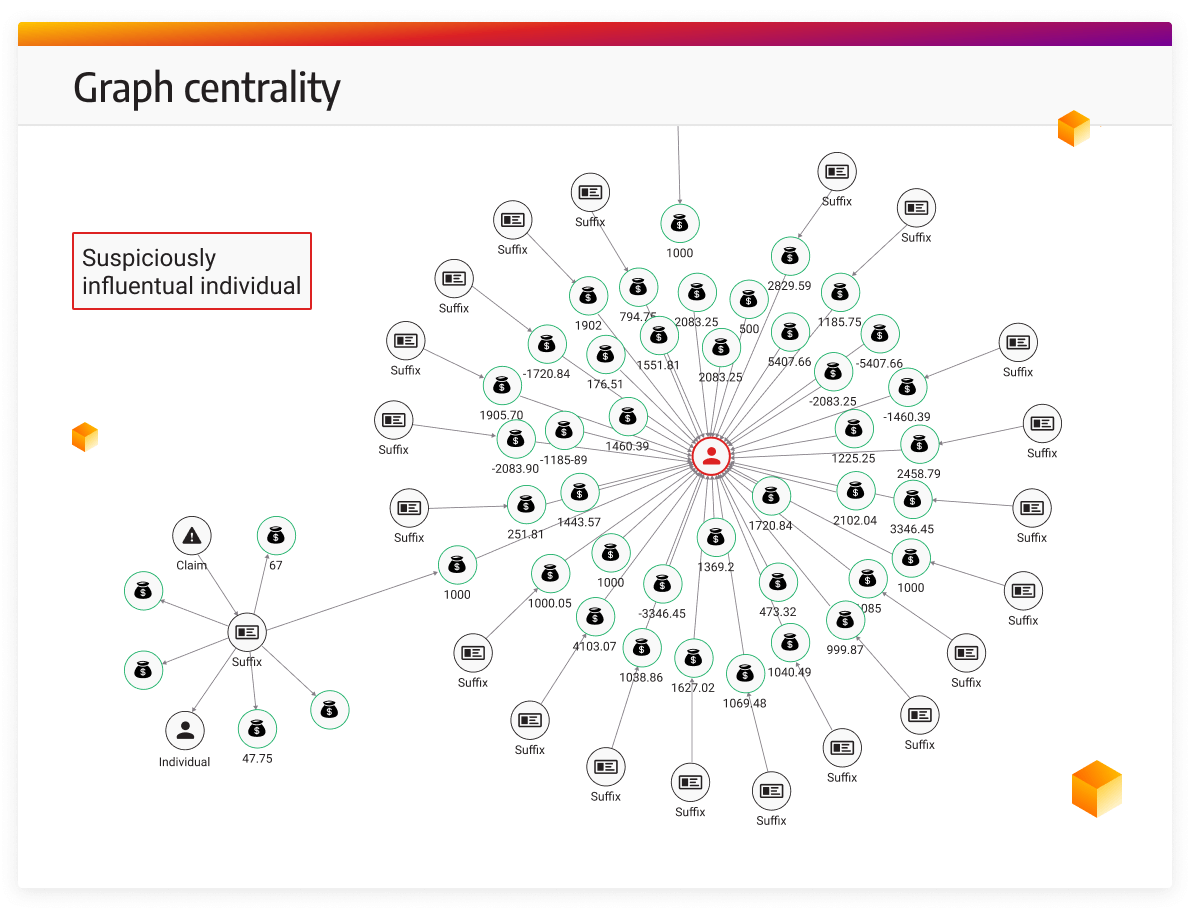
- Community Detection Algorithms → detecting clusters within a network.
Community detection algorithms, such as Louvain or Label Propagation, can identify clusters of highly connected nodes within a network. This is useful for detecting sub-groups within a criminal organization, identifying cells in terrorist networks, or spotting clusters of fake accounts in an identity theft operation. Available through the MAGE library.
- Weakly Connected Components → finding disconnected parts of a network.
This algorithm identifies all weakly connected parts of a graph. In a criminal investigation, it can help identify groups that may not be directly connected but are part of the same larger network. It’s particularly useful for spotting hidden or isolated cells in terrorist or criminal organizations. Available through the MAGE library.
- Strongly Connected Components → identifying highly connected groups.
This algorithm finds groups of nodes where there is a direct, bi-directional connection between every pair. It’s valuable for identifying tightly-knit criminal groups that frequently interact with each other. Available through the MAGE library.
- Similarity Algorithms → finding similar nodes (e.g., suspects, patterns).
Similarity algorithms, such as Jaccard Similarity or Cosine Similarity, can detect similarities between nodes in a graph. This is useful for finding suspects who share common patterns in behavior, communications, or transactions. Available through the MAGE library.
Visualizing Crime Networks with Memgraph Lab
Memgraph Lab’s visualization capabilities can be applied to criminal networks. Investigators can visualize connections between individuals, communication patterns, and transactions in real time.
For instance:
- Visualize the most connected individuals in a criminal organization.
- See the frequency of communications between certain individuals, flagged for suspicious activity.
- Track real-time movement patterns based on GPS data or phone call locations.
The ability to style nodes and edges based on specific properties (as demonstrated with the Tube line colors) is particularly useful in highlighting key individuals or urgent cases. For example, suspects in high-priority investigations could be visually emphasized with larger nodes or different colors to stand out in the network.
We’ve had a similar example but using Memgraph Lab to display complex transportation networks—Modeling, Visualizing, and Navigating a Transportation Network with Memgraph.
Conclusion
Memgraph is a powerful tool for crime-fighting because it excels at connecting the dots in real time. Its ability to handle complex networks, it’s a great asset for law enforcement. With features like high-throughput querying, scalability, and intuitive visualization through Memgraph Lab, investigators can quickly uncover key players, visualize criminal connections, and act fast on live data. Whether you’re working on a small case or tackling an international network, Memgraph has the tools you need to process and visualize the web of crime in ways traditional databases simply can't match.