
How Graphs Solve Two Biggest Problems of Traditional IAM Systems
Identity and Access Management (IAM) includes technologies and processes that enable organizations to provide users with appropriate access to systems, apps, and data. In other words, it defines who gets access to what, for what reason, and at what time. The definition of identity and the individual structure of each organization defines the access management and, therefore, the company’s IAM.
When a current IAM system becomes slow and static it means that it can no longer adapt to the ever-changing team roles and permissions to resources. At that point, there is no need to panic because there are new technologies out there that can avoid the security crisis. Graph databases are at the top of the list. The following post will show how graph databases can tackle the two most important requirements of modern business organizations in dealing with identity and access management.
The idea of identity and hierarchical structures within a company
In the company’s digital world, everything has an identity, but it’s not just passwords and usernames anymore. People are defined by their various identities - consumer, customer, or partner - all within the same organization.
Moreover, things such as smartphones, printers, and other devices also have an identity of their own. In a business environment, increasingly rich and deep relationships emerge between people and people, people and things, and things and services. Entities are becoming more interconnected.
All of these connections are reflected in applications and services, and linking the correct identities plays an important part in the company's security. Not securing those interactions properly represents a tremendous privacy and cybersecurity risk.
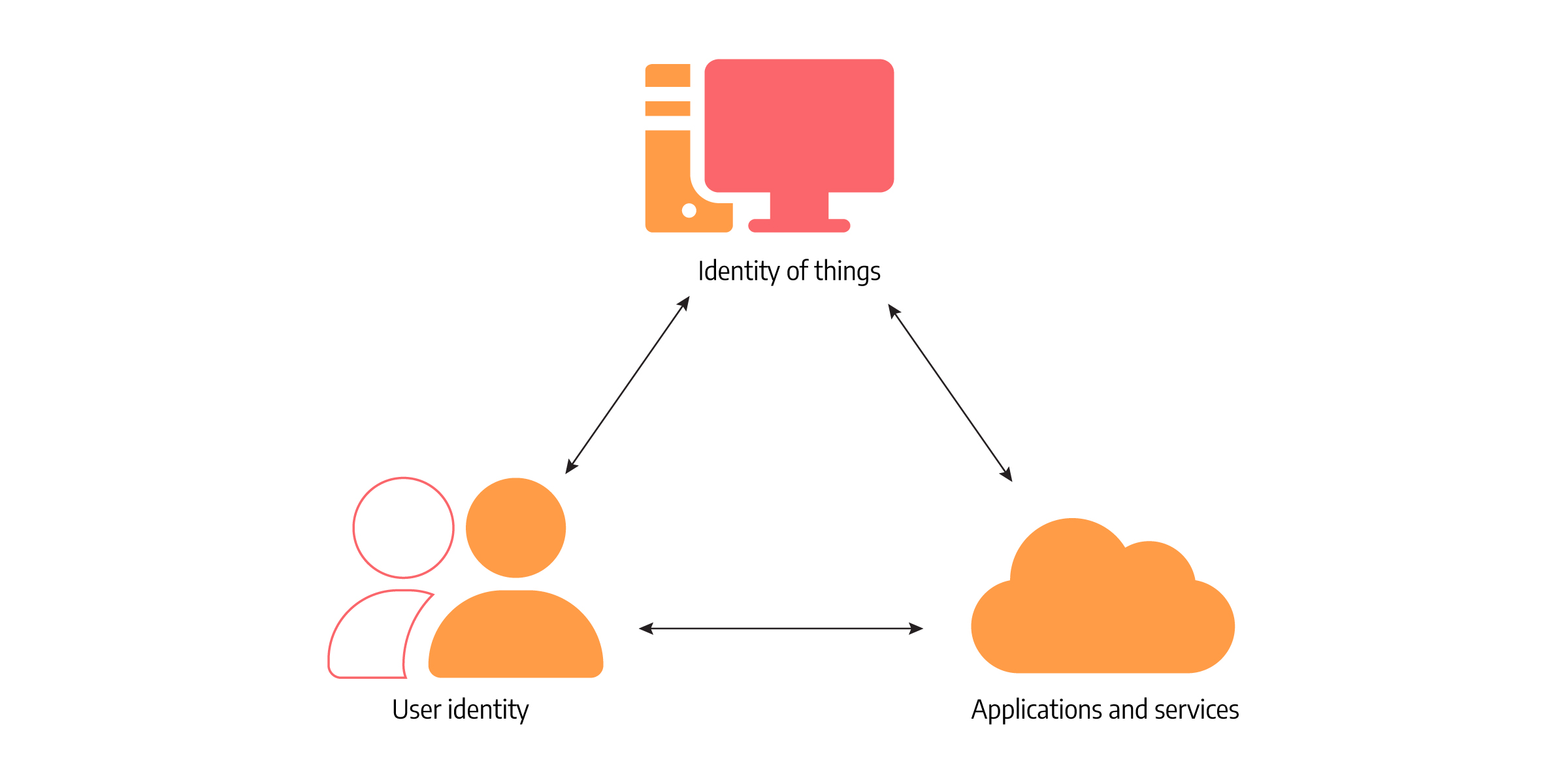
But the issue isn’t just about security. It also boils down to leveraging relationships between all these people and things and providing richer experiences to users. There are many different scenarios to play out, i.e., cloud API access points, data accessing from different devices, and so on. And that is the main reason why it’s essential to keep track of digital identities and connect them properly.
Until now, IAM systems have been defined by rigid hierarchies within organisations. But things are changing. It’s becoming difficult to find a company without cross-functional and changing teams. Because of the changing roles within the company, people at the same hierarchy level can have different access rights, which is hard to shape, model and manage in a strictly hierarchical structure.
Issues IAM systems face
That is exactly what traditional IAM systems have a problem with - the static idea of identity and the underlying assumption that organizations are hierarchical.
The static idea of identity presumes that the permissions of individuals change only upon hiring, switching teams, or leaving an organization. But for modern companies, identity changes are happening much faster. The fast pace of changes and the challenge of securing rights for correct individuals present an issue for static identities. Identity should be more intelligent, more active, and more adaptive.
So the first problem with traditional IAM systems is connected to the fast-paced changes and the inability of identities to adapt to those changes promptly.
The next problem stems from using rigid hierarchical structures when business and social interactions are anything but. The problem worsens because IAM systems still use CSV files to extract data from the HR system or import users to directories, and CSV files cannot represent flexible non-hierarchical structures.
Those two reasons are why the current identity management systems need to change to become effective again.
“Enterprises that develop mature IAM capabilities can reduce their identity management costs and, more importantly, become significantly more agile in supporting new business initiatives.”
Graph thinking in IAM systems
Graph databases have evolved to handle large amounts of interconnected data. And what we see in IAM systems is a massive explosion of connectivity and value created within enormous networks of interconnected data. Given the increasingly collaborative nature of business and organizations, Identity and Management systems need to think of representing their world more fluidly, and graphs are natural when it comes to representing relationships.
As mentioned earlier, the main problem in Identity and Access Management is who gets access to what. Let’s look at a simplified example of how Identity and Access Management works in terms of graphs.
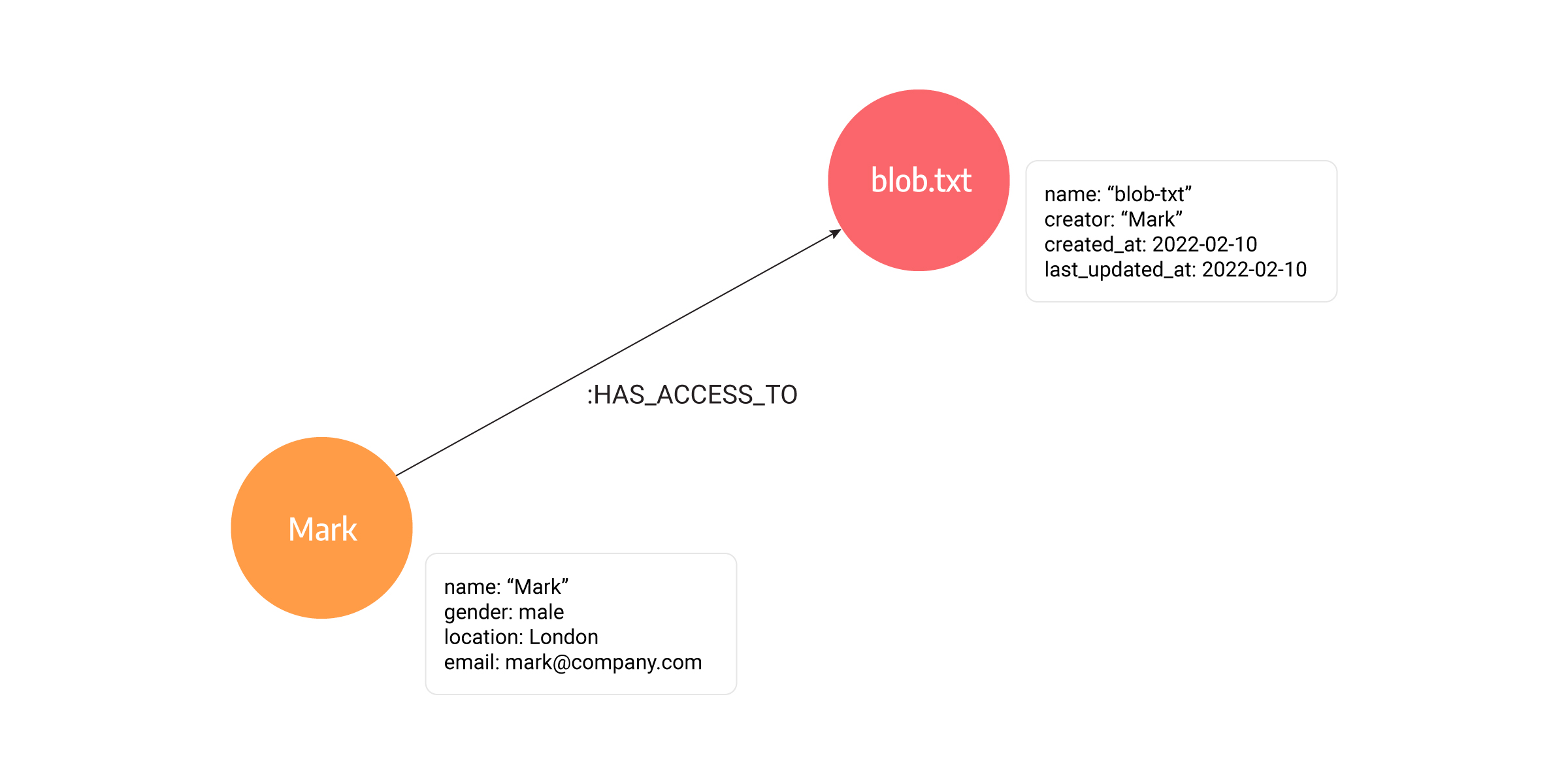
The picture above shows two types of nodes, a Person node and a File node. The File has a few properties like name, creator, created_at, and last_updated_at. On the other hand, a person has properties name, gender, location, and email. The Person and File nodes are connected with a HAS_ACCESS_TO relationship. Graphs enable you to answer the following questions easily:
- whether a person has access to a file
- who can edit a specific file,
- or which files can partners and customers access.
And there are no obstacles to building new nodes and types of relationships with graphs.
Graphs as the solution to rigid hierarchies and static identities
How do graphs tackle the problem of the static idea of identity and rigid hierarchies?
Graphs represent relationships in a much more semantically rich way, allowing accurate views of access rights and simplifying their management, which is impossible to do with a hierarchical structure.
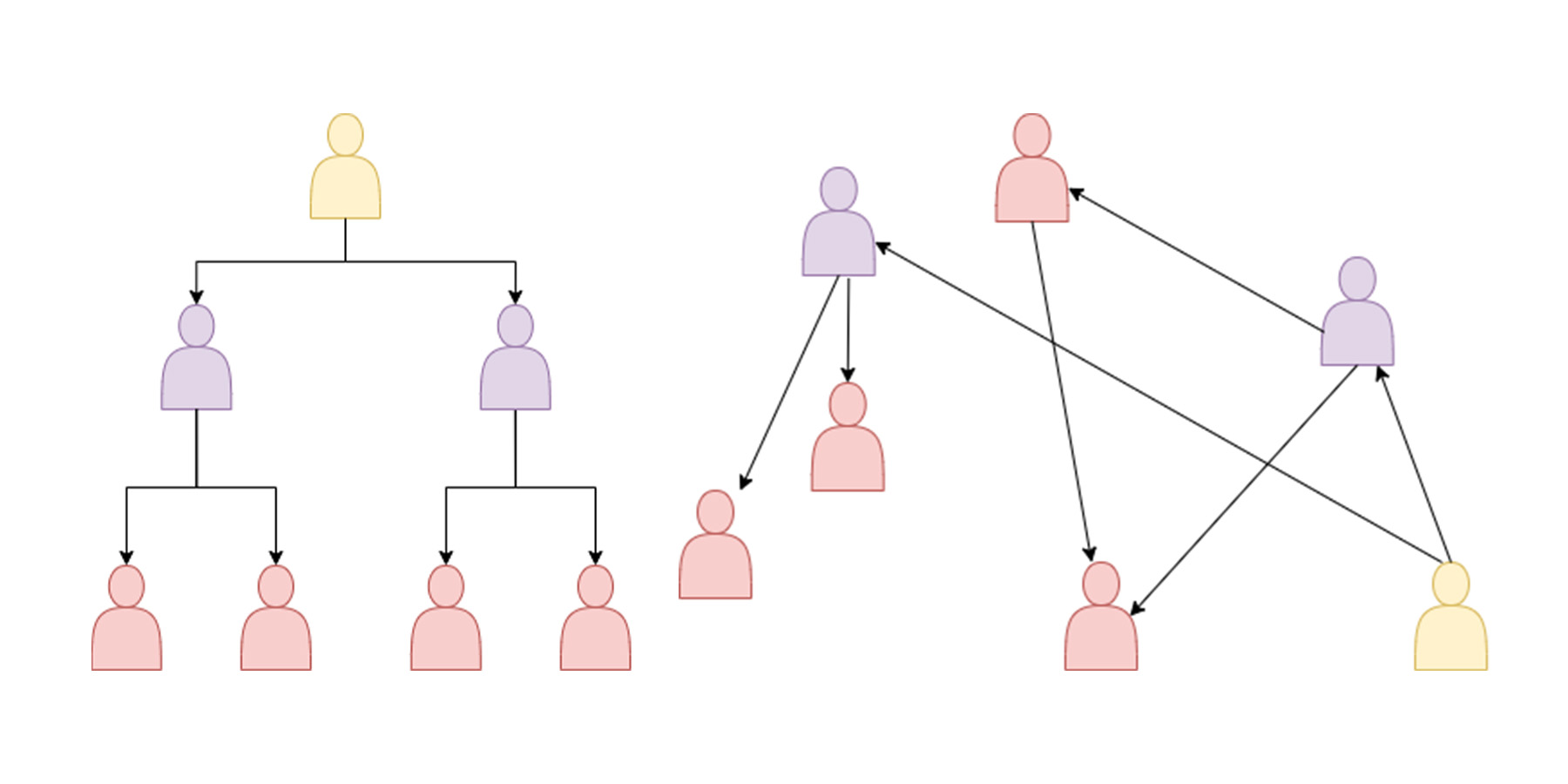
In hierarchies, modifying is complex due to strict structures. Imagine a scenario where a person needs partial access to specific resources. For example, a technical writer needs information from a specific repository only the engineering team has access to. In the antiquated IAM system, that person should be temporarily given permissions as if they were a part of the engineering team. Such powerful permissions represent a vulnerability issue; it doesn’t boil down to a person’s competency but to security and intruders. The more people have unnecessary permissions, the bigger the problem is if an intruder collects their password.
In the picture below, you can see the initial state of mentioned scenario modeled with graphs. We have Mark, who belongs to the Engineering team, and Peter, who belongs to the DevRel team but needs access to a repository to which he usually doesn’t need access. The hierarchical solution would be temporarily making him a part of the Engineering team. But that solution comes with unnecessary risk.
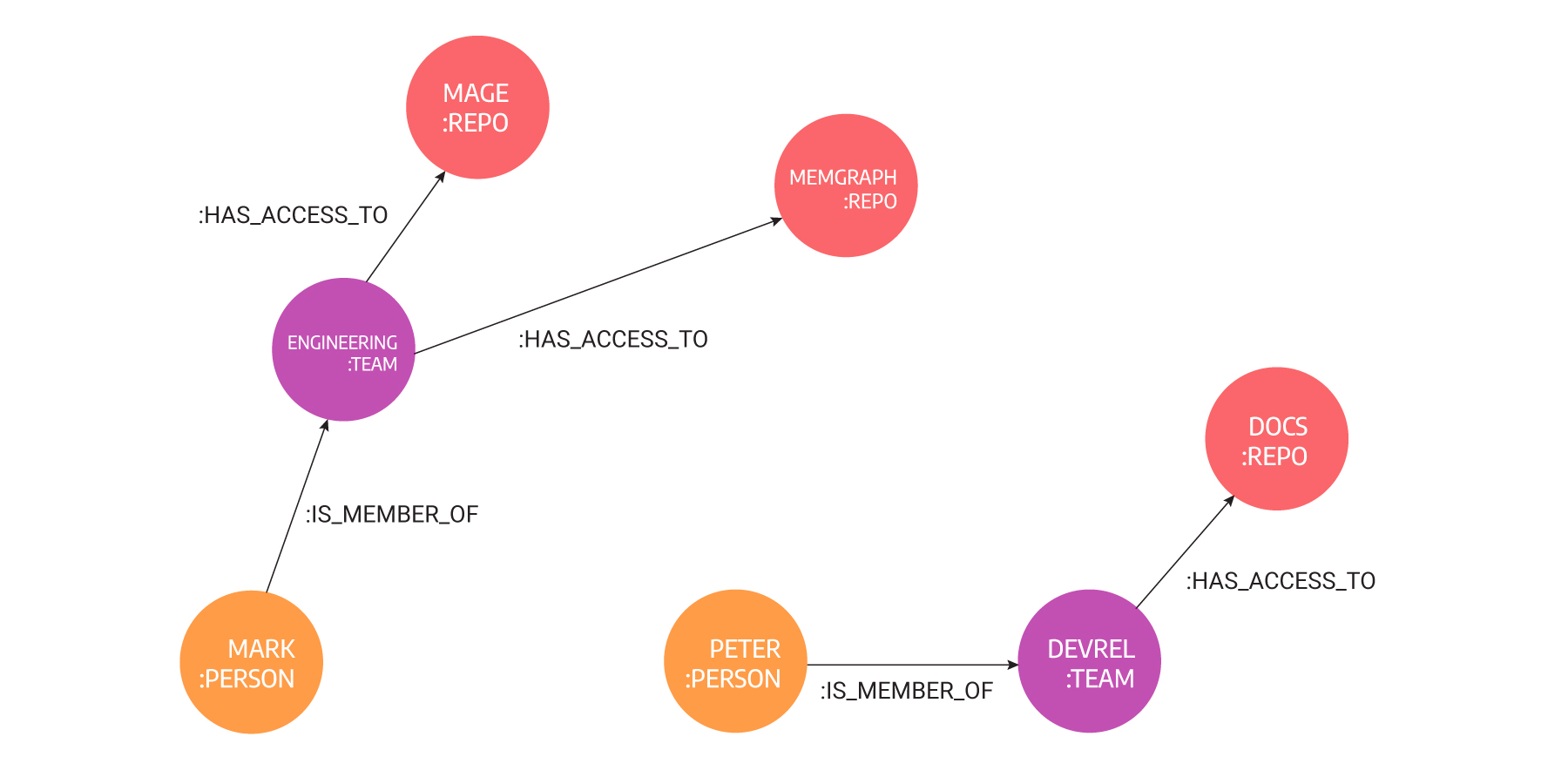
With graphs, it is simple to give access to a specific repository on GitHub or a file without sacrificing security. In the image below, you can see how the situation would be handled with graphs. Peter would be given direct access to Memgraph’s repository without making him a part of the Engineering team.
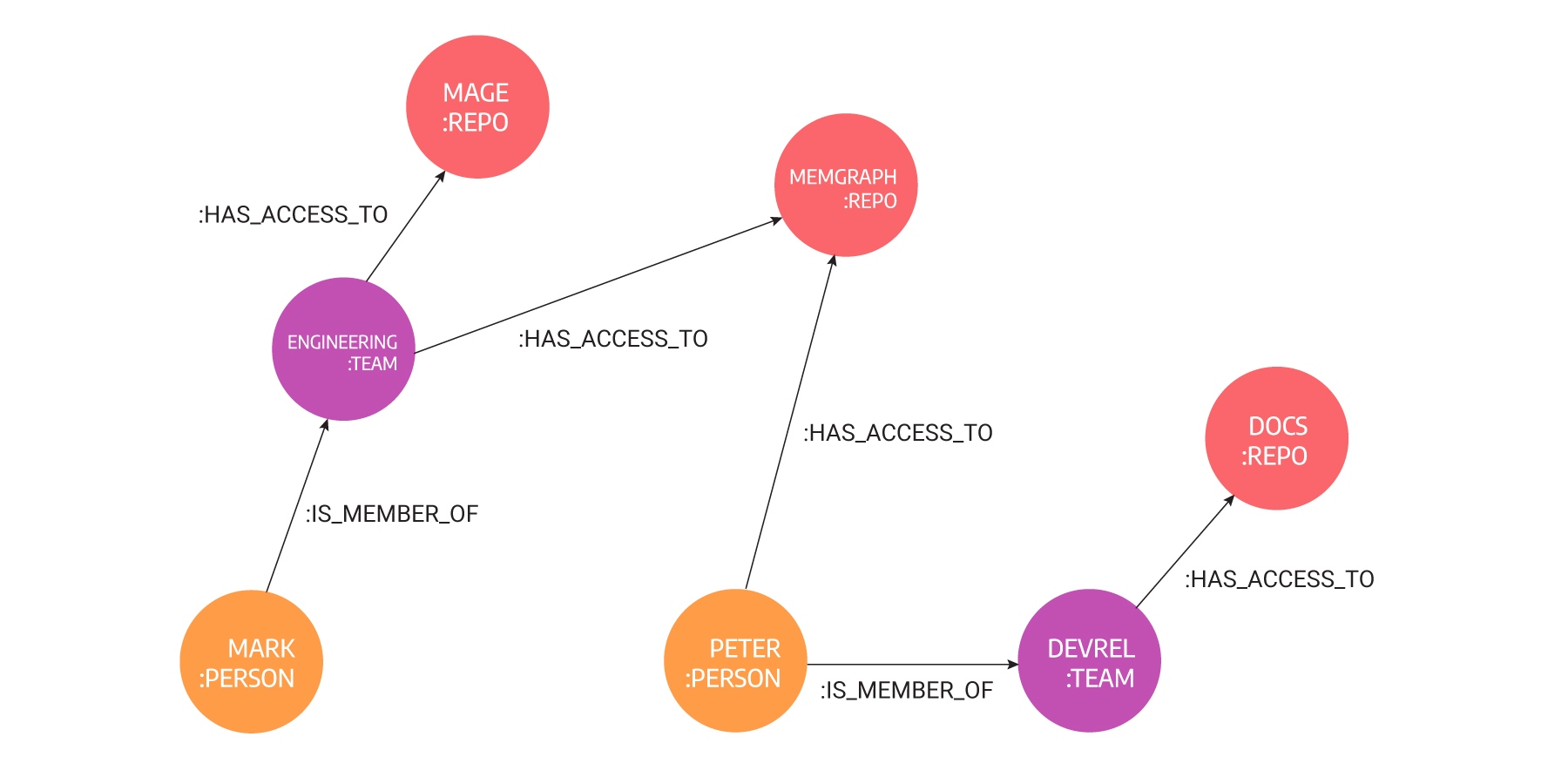
If a person has permissions to access certain resources, a path of maximum two hops exists between that person and that resource. Hop is a jump from one node to the other using outgoing relationships. Graph databases are great for hopping, that is, traversing.
If Peter becomes a part of the Marketing team too, he would have access to all the resources as the rest of the team by doing just one update of the database - adding a new relationship between Peter and the Marketing team. By creating and removing relationships, graph databases mimic the real-life behavior of identity, which is dynamic and adaptive, in one word: modern.
If you are arguing that table JOINs can mimic relationships as well, graph databases do it at least a hundred times faster because there is no need to create relationships while querying, the relationship exists from the moment data was inserted. The query engine of a graph database can traverse millions of nodes and relationships per second.
Graph database access lookups over large, complex structures are executed in milliseconds. As with networks and IT operations, a graph database access control solution allows for both top-down and bottom-up queries about:
- Who are administrators who can manage certain resources, products, services, or users?
- Who are users who have access rights to certain settings?
- Which resource is accessed by end-users?
Graph databases are beneficial for IAM use cases for the following reasons:
- Graph solutions are focused on highly-connected data that comes with an intrinsic need for relationship analysis.
- Graph databases are optimized for data retrieval which is something IAM systems often use.
- Graph databases are ideal for inconsistent data models that demand frequent changes, because graph databases are more focused on the data itself rather than the schema structure.
Conclusion
If your current IAM system is struggling under the pressures of modern-day business requirements, such as frequent changes of teams among employers and daily access demands to various resources, it’s time to move away from the rigid relational databases to the flexibility offered by graph databases. Here’s a to-do list of how to make a smooth transition.
Graph databases provide companies with many benefits, such as data model adaptability, reduce system vulnerability and enable flexibility to the IAM systems. It is why companies are opting for graph databases as their primary Identity and Access management system. Modeling data and updating new policies will never be as easy as it is with graphs and graph databases.