
Memgraph Security Features Explained: Authentication, Authorization, Encryption, and Auditing
Graph database security is crucial because it protects sensitive data from unauthorized access, breaches, and cyber-attacks, ensuring confidentiality, integrity, and availability. Secure databases prevent data theft, financial losses, and reputational damage while complying with regulatory requirements and protecting privacy.
Effective security measures safeguard against data corruption, misuse, and insider threats, maintaining trust in data accuracy and reliability. Robust security supports business operations and decision-making by preventing downtime and ensuring data continuity, highlighting its essential role in safeguarding critical information assets.
Key Graph Database Security Features in Memgraph
Let’s list and explain on a high level the most important features and concepts associated with database security.
-
Authentication ensures only authorized users can access the database by verifying their identity through credentials. In other words, the authentication process verifies that the user is really who they claim to be. This prevents unauthorized access and potential data breaches.
The old-school way of authorizing a user is by checking the password hash (more about that below), but in recent years, more advanced methods become the standard. 2FA (two-factor authentication), multi-factor authentication, and biometrics—just to name a few —are associated with the authentication process.
-
Access control or authorization manages who can access and modify data within the database. Role-based access control (RBAC) and least privilege principles restrict users to only the data and operations necessary for their roles, reducing the risk of data misuse or unauthorized changes.
Often, enterprise organizations require a few well-defined roles for a given database: Admin, Read-Write, and Read-Only. But sometimes, there is a need for much higher granularity rules. In a label-property graph (LPG) database, these rules can be defined by Clause, Label/EdgeType, and Property.
-
Encryption protects data at rest (stored data on disk) and in transit (data being transferred over the network) by converting it into a secure format that can only be read with the correct decryption key. This ensures that even if data is intercepted or accessed unlawfully, it remains unreadable without the proper decryption.
-
Auditing tracks database activities and logs access, modifications, and other significant events. This helps detect suspicious activities, ensure compliance with regulatory requirements, and provide forensic evidence in security incidents.
How Database Security Features Work in Memgraph?
Authentication
In an enterprise environment, it’s crucial to restrict access to authorized personnel only. Memgraph supports a highly secure username/password system and can be configured with centralized external systems such as PAM, LDAP, or single sign-on (SSO) providers such as EntraID or Okta.
Memgraph allows configuring user password strength by specifying a password strength regex. If there is a custom authentication procedure, a custom Auth Module can also be created.
An important aspect of authentication is performance. (I have to mention it here since Memgraph cares deeply about performance 💪🏻).
When authenticating users, passwords are not used directly; instead, password hashes are used to avoid storing sensitive passwords. Various hashing functions are available:
bcrypt: Offers the best security but with significant performance cost.sha256: Faster but less secure.- Multiple
sha256applications: A middle ground providing higher performance with adequate security.
Memgraph supports all three options to balance security and performance.
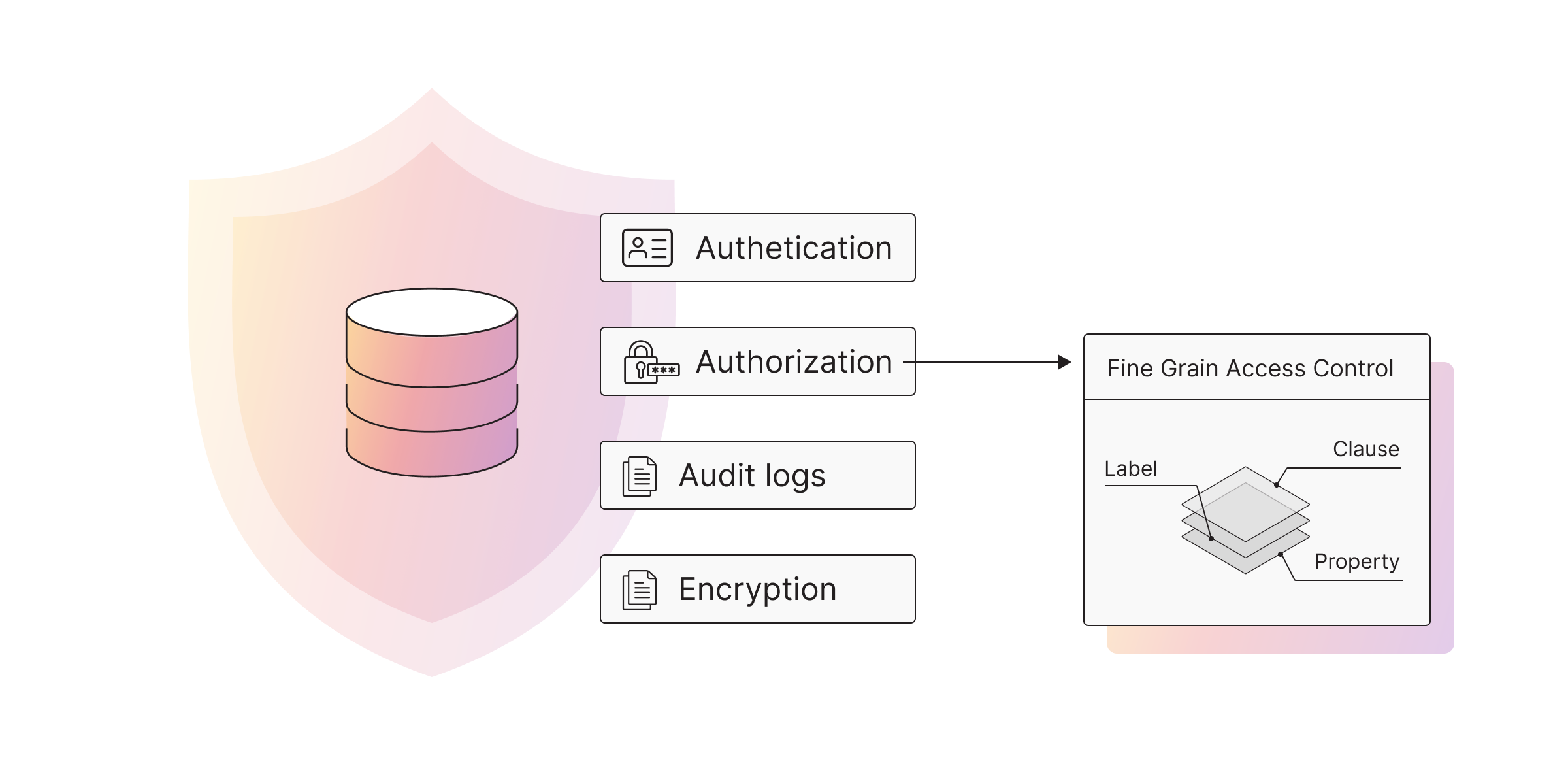
Access Control or Authorization
It’s impossible to talk about authorization without being specific about the system that is providing access control rules. Since Memgraph is a label-property graph (LPG) DBMS, authorization was designed to fit that data model.
There are three levels on which it’s possible to define access control rules inside Memgraph.
-
Clause-based authorization operates on the database query level. By assigning clause-specific privileges (such as
MATCH,CREATE,MERGE, etc.) to a given user role, specific access control rules can be defined. It’s possible to define arbitrary user roles. Most often, applications have roles such asAdmin,Read-Write, andRead-only. These types of access control rules are defined on the clause level. -
Label-based authorization (also includes Edge Type) operates on the “tags” associated with each node or edge in the graph (called labels or edge types). This is considered fine-grained access control because it depends on the stored data. It’s possible to create very advanced access control rules on this level. Some users are even considering implementing a multi-tenant system just by creating good enough label-based access control rules.
-
Property-based authorization (coming soon) operates on the property level (key-value pairs associated with each node or edge in the graph). It’s very granular and sometimes required, but it usually comes with significant memory and/or performance overhead because the database system has to store information about each property (e.g., each node can have hundreds of properties).
Encryption
Memgraph ensures data protection during transit through industry-standard encryption libraries. Memgraph’s implementation of the Bolt protocol supports TLS encryption, while HTTPS could be used for other connections.
You typically deploy databases within a protected VPN. For optimal performance, it's best to avoid encryption. However, when encryption is necessary, Memgraph provides robust data protection. The key aspect of encryption in transit is ensuring you have the right certificate authority to secure your deployment.
While Memgraph does not include native at-rest encryption, users can configure this feature using tools like the Linux Unified Key Setup (LUKS), providing flexibility to meet various security requirements. It’s important to emphasize that the most important aspect of encryption at rest is key management. Solutions like LUKS come with battle-tested options to manage your keys securely.
Auditing
Memgraph handles auditing (also known as audit logs) by writing all executed queries into a separate file. This process is similar to regular database logging but includes different data points. Currently, Memgraph stores the timestamp, IP address, username, query, query parameters, and database name.
Typically, users ship audit logs to a centralized system for storage and later use, such as Splunk. The team plans to offer tighter integrations with systems dedicated to audit log management.
Conclusion
And that’s it for now. Hopefully, this was insightful. For more detailed insights and technical specifics, explore the Memgraph Docs pages.
Next Steps
Now that you're familiar with our security enterprise features, it's time to experience them firsthand. Get the fully featured 30-day free Enterprise trial with no strings attached and properly test out Memgraph. If you have further questions or need personalized assistance, book a 30-minute session with one of our engineers from the DX team.
Further Reading
This blog post is part of the "Memgraph is Enterprise-Ready" series. Be sure to check out the other articles:
- Product announcement: Memgraph Is Enterprise-Ready
- Blog post: Memgraph Operational Features Explained
- Blog post: Announcing Memgraph's High Availability Automatic Failover: Developer-Ready
- Blog post: Announcing: Memgraph as a Multi-Tenant Graph Database