
What's The Role of Graph-Powered IAM Analysis in Cybersecurity
Permissions, roles, and access rights are at the heart of any cybersecurity strategy. But when they’re tangled, misconfigured, or just forgotten, they turn into risk points.
Attackers know this. They don’t always use obvious entry points; sometimes, they access overlooked accounts or indirect pathways that go unnoticed. Shadow admins, orphaned accounts, indirect permissions. These are the gaps static IAM tools fail to catch.
Graphs close those gaps by giving you the missing context. In this article, you’ll learn exactly how.
The Problem: IAM Isn’t a Simple Hierarchy
Most companies still rely on static IAM dashboards and audit lists. This might work if access rights are simple and straightforward. But in reality, access is layered and indirect.
A single permission can be inherited through multiple teams, roles, and nested groups. An account that looks low-privilege can end up with admin rights through overlapping memberships. And misconfigured accounts often stay hidden because there is no clear visibility into how they connect to critical systems.
That’s how privilege escalation happens. And that’s exactly how attackers move laterally once they’re inside.
The Graph Approach: Visualize Access Clearly
Graph databases help counter this lack of visibilty.
They treat every user, role, device, app, and resource as nodes. Every relationship is a connection. So you don’t lose detail or get forced into oversimplified hierarchies.
With this structure, you can:
- Map direct and indirect permission paths.
- See exactly how a user inherits access to sensitive resources, even if it crosses multiple teams.
- Identify accounts that serve as hidden gateways between systems.
- Spot dormant accounts with permissions that are still active.
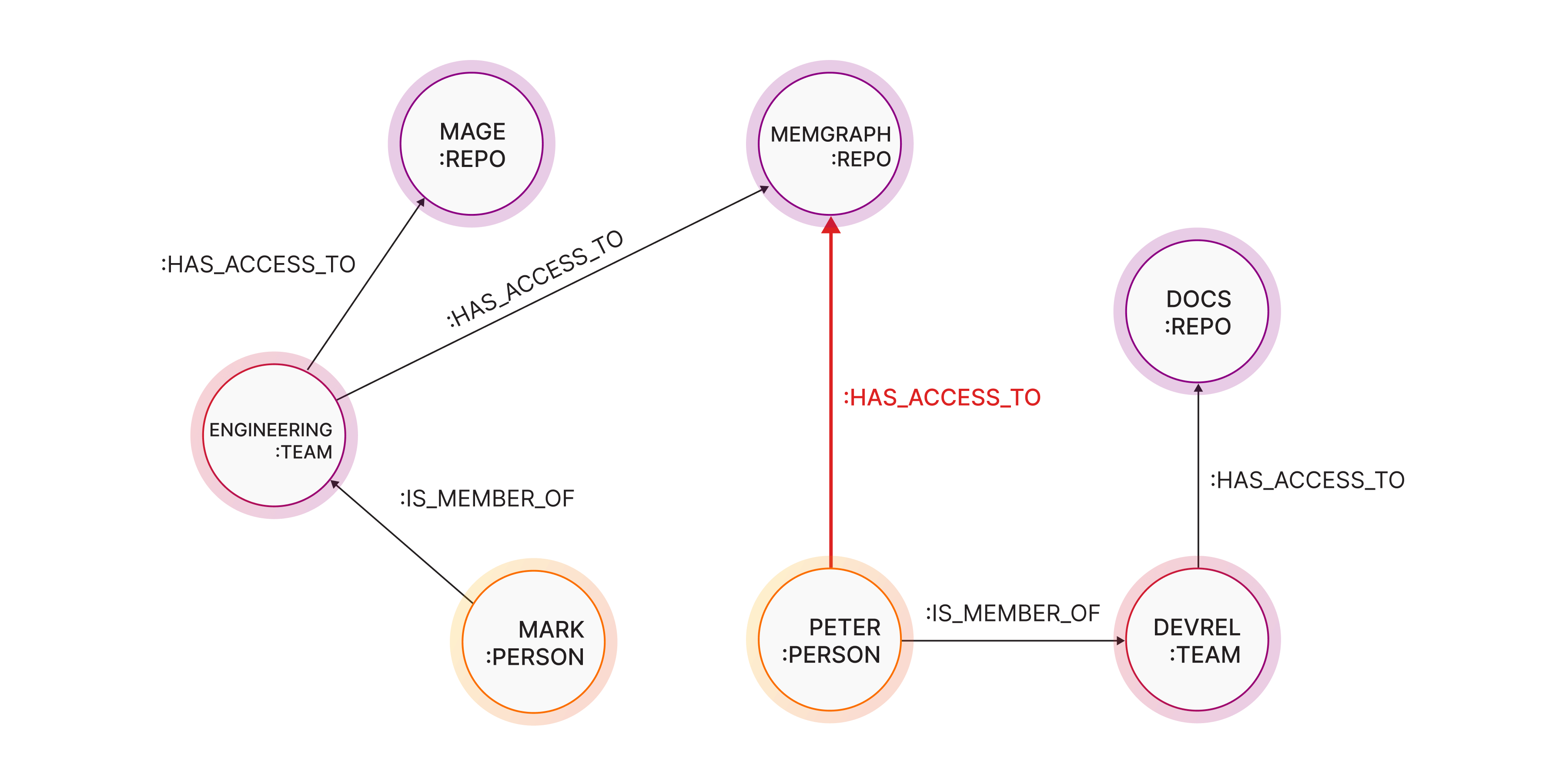
Let’s make it real. Here’s a simple example:
Say at Memgraph, Peter, an employee, is not a part of the engineering team but still has access to the Memgraph repository. How? Through indirect group memberships and leftover permissions.
With the flexible schema of graph databases, this connection can be stored and clearly visualized. It is possible to have a direct connection between Peter and Memgraph repository without any need for a specific relationship structure (such as Person -> Team -> Repo).
Why It Matters: Small Missteps, Big Breaches
The 2024 IBM Cost of a Data Breach Report found that stolen or compromised credentials account for 16% of breaches, making them the #1 entry point.
That’s not an accident. Over-provisioned permissions. Forgotten accounts. Shadow admin rights that grow over time. These are exactly what attackers hope you won’t notice.
Graph tech for IAM systems make these hidden pathways visible. They help security teams run what-if scenarios: What happens if this low-level account is compromised? They help you tighten access paths and catch risky privilege escalation before it costs you millions.
Unfolding the LastPass Breach
Take the 2023 LastPass breach. Attackers stole credentials from a senior DevOps engineer’s personal device. But the breach didn’t stop there.
They used those credentials to move laterally through under-monitored pathways. They found indirect access to a shared cloud storage environment that held customer vault backups.
Those paths were right there in the identity network. They just weren’t visible.
Graph-based IAM analysis closes that gap.
The Analyst’s Edge: Graph Algorithms in Action
Graphs don’t just help you store connections. They help you analyze them. Here are some key algorithms useful for IAM analysis:
| Betweenness Centrality | It finds accounts that act as gateways between multiple systems or permission groups, indicating potential insider threats. |
| Degree Centrality | It detects over-permissioned or overly connected identities. |
| Community Detection | It groups users with similar access patterns to identify outliers. |
Visualizing the Threat: Mapping Least-Resistance Paths to High-Value Targets
Attackers look for the shortest, least protected paths to valuable data. You should, too.
In real-world IAM analysis, deep path traversal algorithms such as All Shortest Paths are used to uncover the most exploitable access routes or “paths of least resistance” from compromised identities to high-value targets (HVTs).
These algorithms help simulate attacker movement across identity relationships, revealing misconfigurations that allow lateral access to sensitive systems.
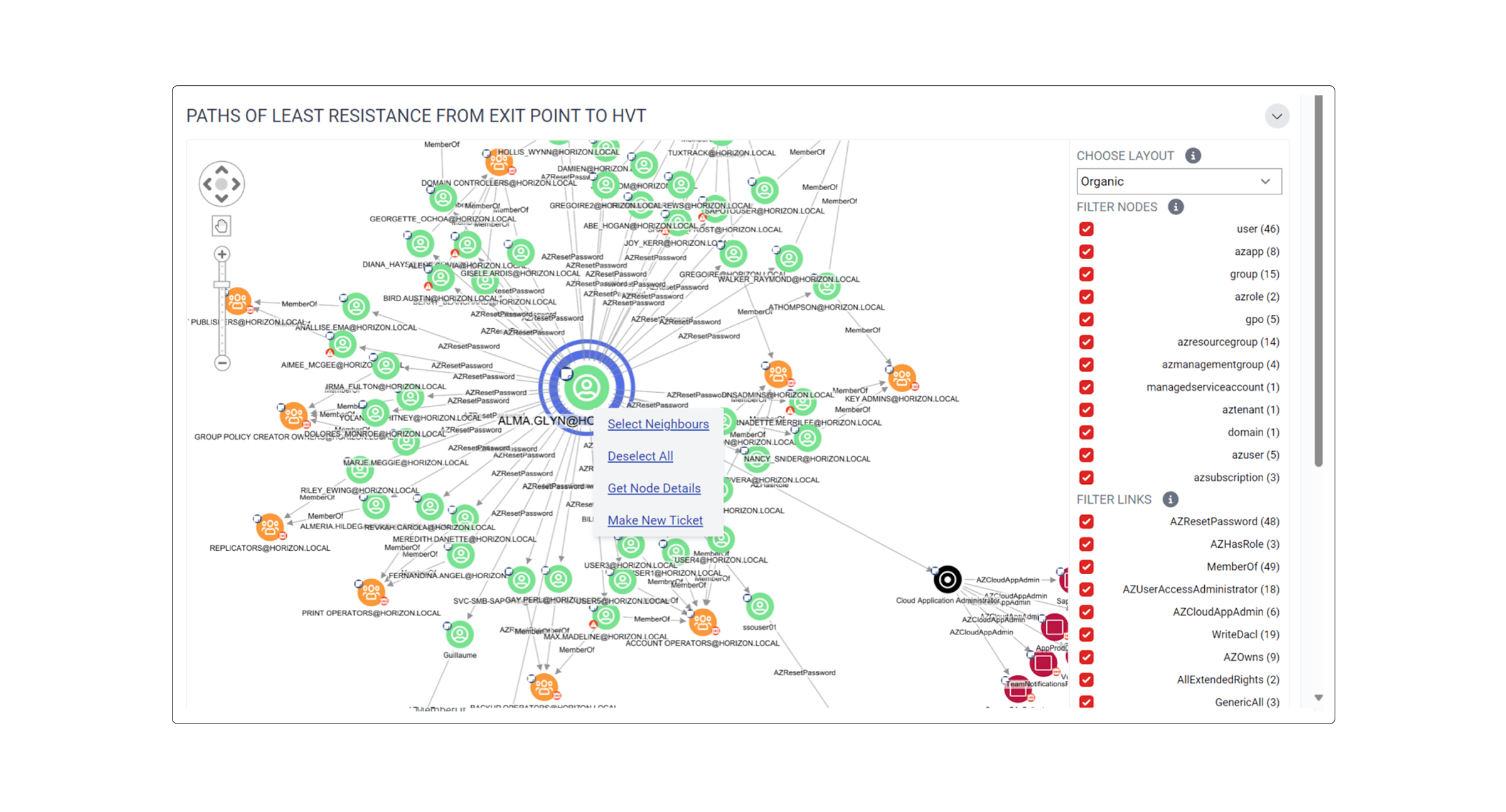
The graph above, from Saporo’s attack path management system, highlights such a path: starting at a low-privilege account (exit point) and traversing through indirect group memberships to ultimately reach an HVT.
Wrapping Up
Identity & Access Management shouldn’t be a once-a-year audit. It’s a real-time system that shifts every time a user joins, leaves, changes teams, or spins up a new tool.
Graph databases help you keep up with that reality. They provide the context you need to ask better questions, trace risky connections, and fix misconfigurations while they’re still just that.
Want a deeper look at all five cybersecurity use cases enabled by graph technology?
Download the full Cybersecurity Guide to explore practical insights and research-backed techniques.